搜索结果: 1-15 共查到“Recovery”相关记录568条 . 查询时间(0.328 秒)
Evaluating Post-Fire Vegetation Recovery in Cajander Larch Forests in Northeastern Siberia Using UAV Derived Vegetation Indices
Larix cajanderi Siberia wildfire drones uncrewed aerial vehicle NDVI GCC normalized difference vegetation index green chromatic coordinate
2023/12/18
The ability to monitor post-fire ecological responses and associated vegetation cover change is crucial to understanding how boreal forests respond to wildfire under changing climate conditions. Uncre...
Molecular and Physiological Responses of Naturally Grown Atriplex halimus L. to Drought-Stress Recovery in the Absence or Presence of Na+ Ions Under Natural Conditions
Atriplex halimus Stress/recovery-inducible genes NaCl Photosynthesis Recovery
2023/12/4
It was suggested that Na+ ions could play a vital role in the growth of xero-halophyte Atriplex halimus. This study aims at investigating the impact of Na+ ions on the response of droughted A. halimus...
Superstructure-Based Simultaneous Optimization of a Heat Exchanger Network and a Compression-Absorption Cascade Refrigeration System for Heat Recovery
Heat Exchanger Network Refrigeration System Heat Recovery
2023/6/19
A heat exchanger network (HEN) plays an important role in the chemical process industry owing to its significant effect in energy recovery. A compression-absorption cascade refrigeration system (CACRS...

Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:Low Rank Matrix Recovery for Seismic Data Analysis and Blind Superresolution
地震数据分析 盲超分辨率 低秩 矩阵恢复
2023/4/19
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:Geometry and recovery of spectral-sparse signals
频谱稀疏信号 几何 恢复
2023/4/26
中国地质大学科学技术发展院王向东(博士研究生),赵来时*等 GPMR国家重点实验室 Earth and Planetary Science Letters(2019), Global mercury cycle during the end-Permian mass extinction and subsequent Early Triassic recovery
晚二叠;纪末;生物;大绝灭;早三叠;生物;复苏;时期;全球;汞循环
2021/10/20
近日,中国地质大学地质过程与矿产资源国家重点实验室赵来时教授团队在Nature Index 杂志——《Earth and Planetary Science Letters》发表题为《晚二叠纪末生物大绝灭及早三叠生物复苏时期全球的汞循环》(Global mercury cycle during the end-Permian mass extinction and subsequent Early...
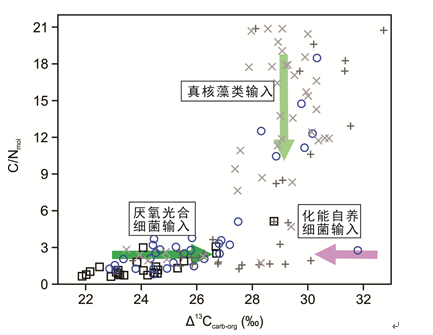
中国地质大学科学技术发展院杜勇(博士生),宋虎跃*等,BGEG国家重点实验室. GSA Bulletin (2021), Changes in productivity associated with algal-microbial shifts during the Early Triassic recovery of marine ecosystems(图)
海洋高温;缺氧;动荡;碳;循环过程
2021/10/15
近日,地质学著名期刊《Geological Society of America Bulletin》正式刊发了中国地质大学宋虎跃副研究员团队的研究成果“Changes in productivity associated with algal-microbial shifts during the Early Triassic recovery of marine ecosystems”,该论文第...

Coral recovery during a prolonged heatwave offers new hope(图)
Coral recovery during prolonged heatwave offers new hope
2020/12/25
Some corals managed to survive a globally unprecedented heatwave, report scientists in a study that provides hope for the long-term survival of coral reefs."The devastating effects of climate change o...

Scientists improve understanding of Mount St. Helens eruption recovery(图)
Scientists Mount St. Helens eruption recovery
2020/2/20
Through research in the blast zone of Mount St. Helens, Evergreen State College scientists have discovered that plants are influencing the ecosystem’s recovery.A new paper reporting the results, "Plan...

The fate of the world's coral reefs could depend on how well the sea creatures equip their offspring to cope with global warming.About half the world's coral has been lost due to warming seas. Rather ...
We show that Legendre PRF, recently suggested as an MPC-friendly primitive in a prime field ZpZp, admits key recovery attacks of complexity O(p√)O(p) rather than previously assumed O(p)O(p). We also d...
Plaintext Recovery Attacks against XTS Beyond Collisions
XTS Storage encryption Mode of operation
2019/7/17
XTS is an encryption scheme for storage devices standardized by IEEE and NIST. It is based on Rogaway's XEX tweakable block cipher and is known to be secure up to the collisions between the blocks, th...
Forward Integrity and Crash Recovery for Secure Logs
cryptographic protocols computer systems
2019/5/21
Logging is a key mechanism in the security of computer systems. Beyond supporting important forward security properties, it is critical that logging withstands both failures and intentional tampering ...
Practical Key-recovery Attacks on Round-Reduced Ketje Jr, Xoodoo-AE and Xoodyak
Conditional Cube Attack Keccak Ketje Jr
2019/5/9
Conditional cube attack was proposed by Huang et al. at EUROCRYPT 2017 to attack Keccak keyed mode. Inspired by dynamic cube attack, they reduce the degree by appending key bit conditions on the initi...


